Sunday, January 31st, 2010 (
No comments yet)
What It Is
Because businesses online quickly figured out that sending names, passwords, credit card details, and other sensitive information out unprotected over the Internet was a bad idea, SSL was implemented.
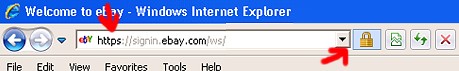
SSL, or Secure Sockets Layer, is an encryption technique that's already built into your browser. You can see in the screenshots for Firefox and Internet Explorer here where 1) the HTTP in the address bar is listed as HTTPS (where the S stands for "secure") and 2) there is a lock icon (at the bottom right of the window for Firefox and just to the right of the address bar for IE).
Why to Use It
Nothing on the Internet was designed with security in mind, all of it was added as an afterthought. So think about this: when you hit the "Submit" button on any webpage, you're sending data from your computer to theirs, but the Internet is a vast inter-connected web of computer systems that spans the entire globe. Somewhere between you and them could be someone monitoring the traffic.
If someone's listening in, they can look right at your data and take your name and password or any other sensitive data you sent. What happens if someone took your name and password and logged into your mail, your bank, or any other service? They could embarass you, spam people from your account, take your money, etc.
Any time you're about to log in or send form data for an account or online order, make SURE that the HTTPS is active. In some cases, you might have to use a trick or too to turn it on. As in these cases:
Case 1: Finding the option for enhanced security and clicking it.
Case 2: Using my login trick to activate security.
When to Use It
You are most at risk when using hotspots at hotels, airports, and cafe's. Consider that the hotel itself or at least all the people there have access to the wireless networking equipment you connect to. Since you are going through them for Internet, they can easily see anything and everything you send. The same goes for your Internet service provider and many of the people who work for them (though you might assume, right or wrong, that the ISP has better physical protections and auditing to prevent their employees from doing it).
Take blind faith out of the equation and make sure HTTPS is active instead!
Limitations
When you see HTTPS, it means you have a mostly secure end-to-end connection, but the first problem is that SSL isn't absolute security. It's way better than nothing, but if something you're sending is absolutely critical to you, maybe you should call it in instead.
Second, bad guys with fake websites can get SSL security too. All that happens then is you have a very secure connection between you and the guy that's going to rip you off. The first defense against this is to use my trick to avoid bogus websites in the first place.
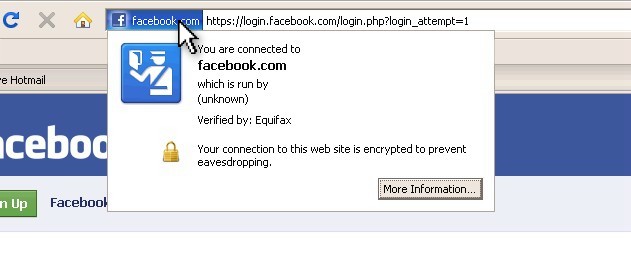
The second tip is to just click the certificate itself to learn more about where you are. Click the colored area to the left of the address (for Firefox) or to the right of the address where the lock Icon is (for IE).
This popup window shows you who the secure connection belongs to and who is validating that fact. In one, Equifax is verifying that the page you're on is Facebook.com while VeriSign is validating that you're on eBay.
 |  | Always remember to look for HTTPS whenever logging in or entering other important data online. If it's not there, maybe you should think twice about clicking SUBMIT. |
Tags:
Facebook,
Shopping Online,
Social Networking















 Between April 2007 and January 2008, visitors to the Kmart and Sears web sites were invited to join an "online community" for which they would be paid $10 with the idea they would be helping the company learn more about their customers. It turned out they learned a lot more than participants realized or that the feds thought was reasonable.
To join the "My SHC Community," users downloaded software that ended up grabbing some members' prescription information, emails, bank account data and purchases on other sites. Sears called the group that participated "small" and said the data captured by the program was at all times secure and was then destroyed.
Between April 2007 and January 2008, visitors to the Kmart and Sears web sites were invited to join an "online community" for which they would be paid $10 with the idea they would be helping the company learn more about their customers. It turned out they learned a lot more than participants realized or that the feds thought was reasonable.
To join the "My SHC Community," users downloaded software that ended up grabbing some members' prescription information, emails, bank account data and purchases on other sites. Sears called the group that participated "small" and said the data captured by the program was at all times secure and was then destroyed.